July 17, 2020 / Nirav Shah
For any website or an application, security is always the top priority. To equip you with such knowledge on the AWS ecosystem, our AWS team experts have already made some amazing articles. If you haven’t checked then the links are listed below.
Now suppose, if you want to restrict a specific domain on AWS S3. Is this possible?
The answer is yes and let’s get started.
Step 1
Login to your AWS Console
Step 2
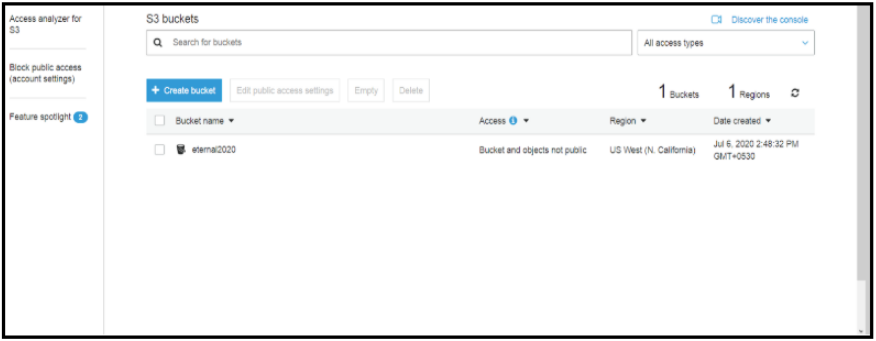
Go to S3 service and create the bucket
Here we will create a bucket named “eternal2020”
Step 3
Go to “permission” section and click on the bucket policy button and create some custom policy. Before we put in custom policy for our S3 bucket, let us consider two scenarios:
Allow requests from a particular domain
Deny requests from a particular domain
#1. In this policy, we can allow requests from only one domain mentioned here (www.example.com or example.com)
{
"Version":"2012-10-17",
"Id":"http referer policy example",
"Statement":[
{
"Sid":"Allow get requests originating from www.example.com and example.com.",
"Effect":"Allow",
"Principal":"*",
"Action":"s3:GetObject",
"Resource":"arn:aws:s3:::eternal2020/*",
"Condition":{
"StringLike":{"aws:Referer":["http://www.example.com/*","http://example.com/*"]}
}
}
]
}
And click “save” button
#2. Now, let see how can we restrict a specific domain (www.example.com or example.com)
{
"Version":"2012-10-17",
"Id":"http referer policy example",
"Statement":[
{
"Sid":"Allow get requests originating from www.example.com and example.com.",
"Effect":"deny",
"Principal":"*",
"Action":"s3:GetObject",
"Resource":"arn:aws:s3:::eternal2020/*",
"Condition":{
"StringLike":{"aws:Referer":["http://www.example.com/*","http://example.com/*"]}
}
}
]
}
Here our bucket name “Eternal2020” and we have restricted or allowed requests from a particular domain to AWS S3 bucket.
Cross-Origin Resource Sharing (Explained with an example)
CORS defines a way for client web applications that are loaded in one domain to interact with resources in a different domain. With CORS support, you can build rich client-side web applications with Amazon S3 and selectively allow cross-origin access to your Amazon S3 resources.
So let see how can we do that
CROS can be found under a separate tab next to the Bucket Policy tab, called CORS configuration.
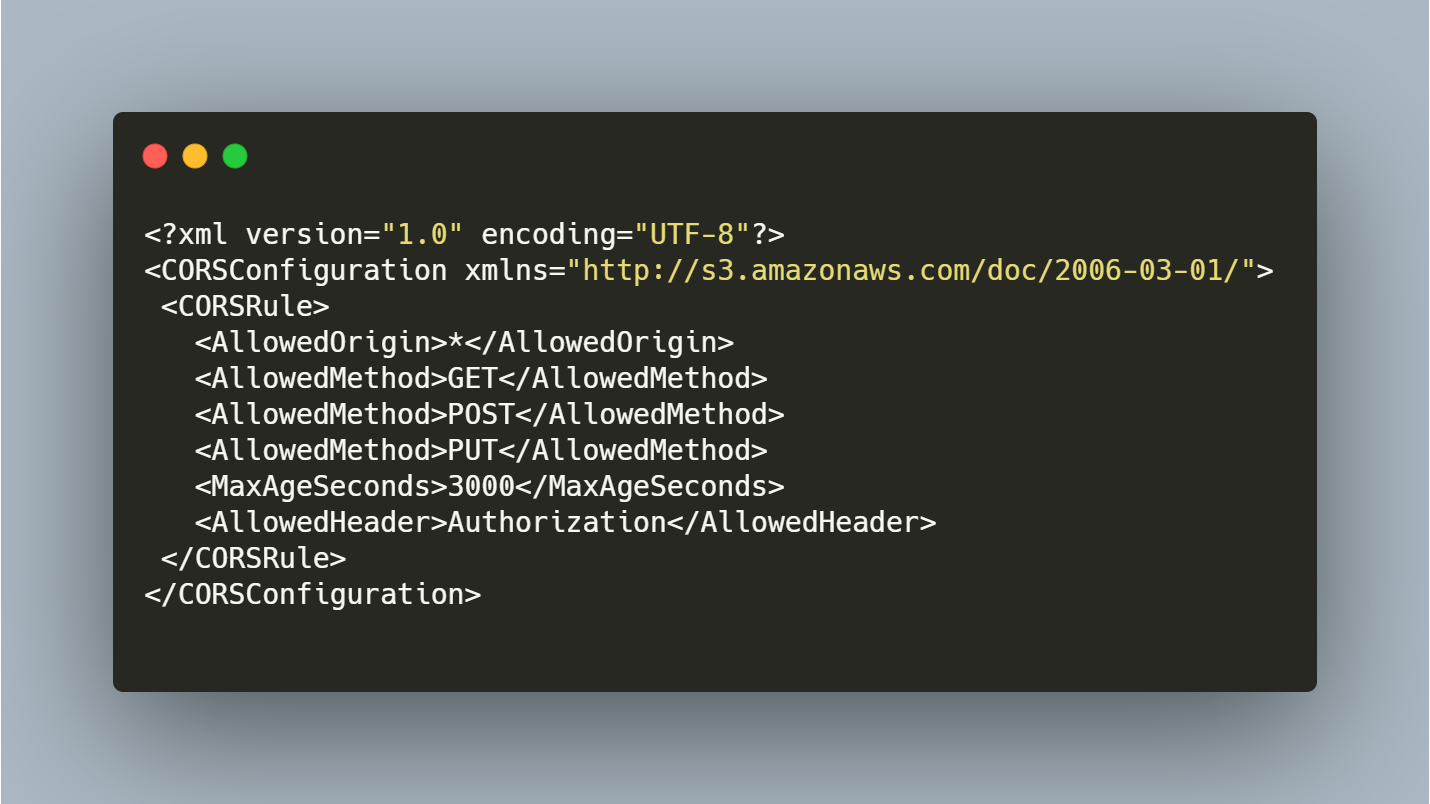
The * means allow access from any source/origin.
Suppose if your domain is like “example.com” so the configuration look it
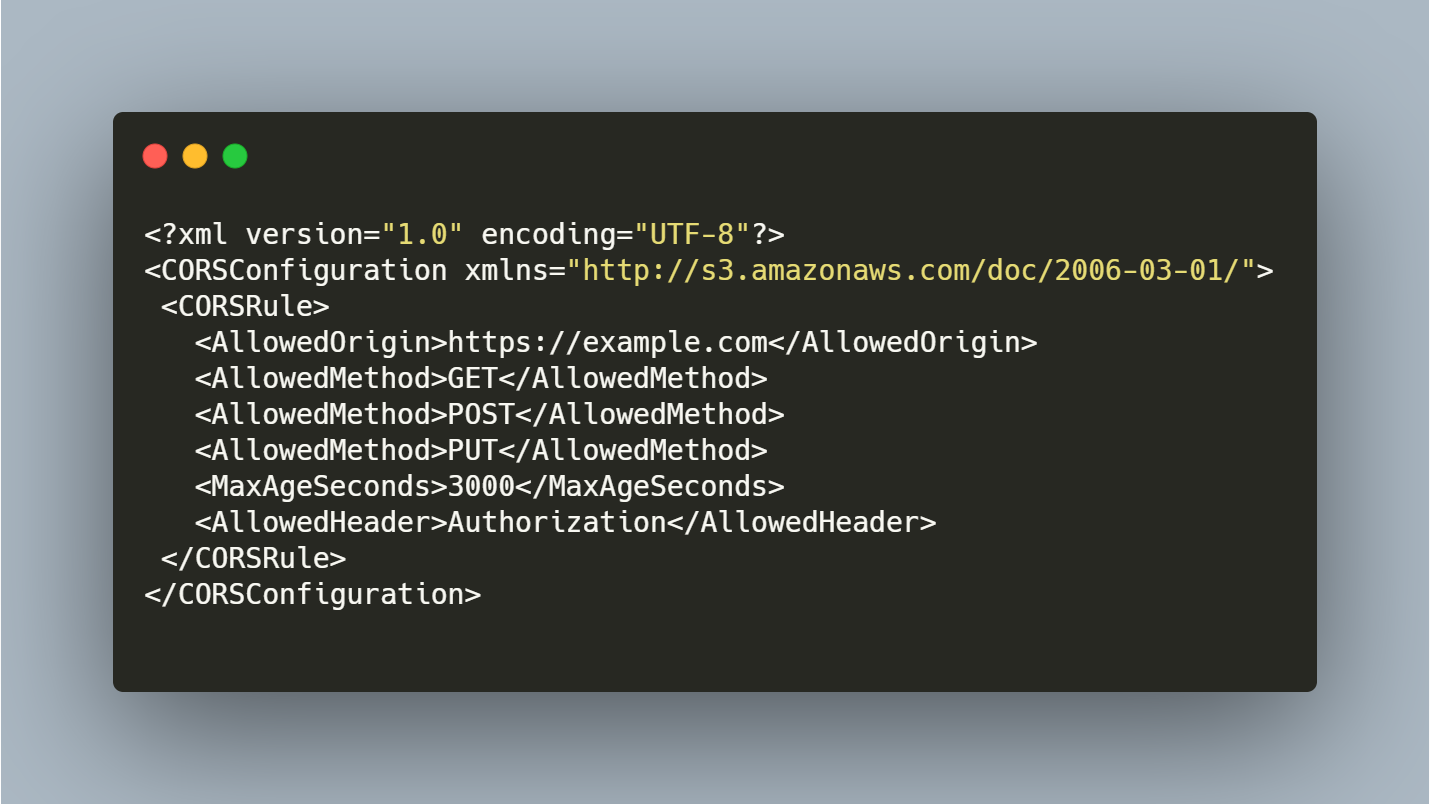
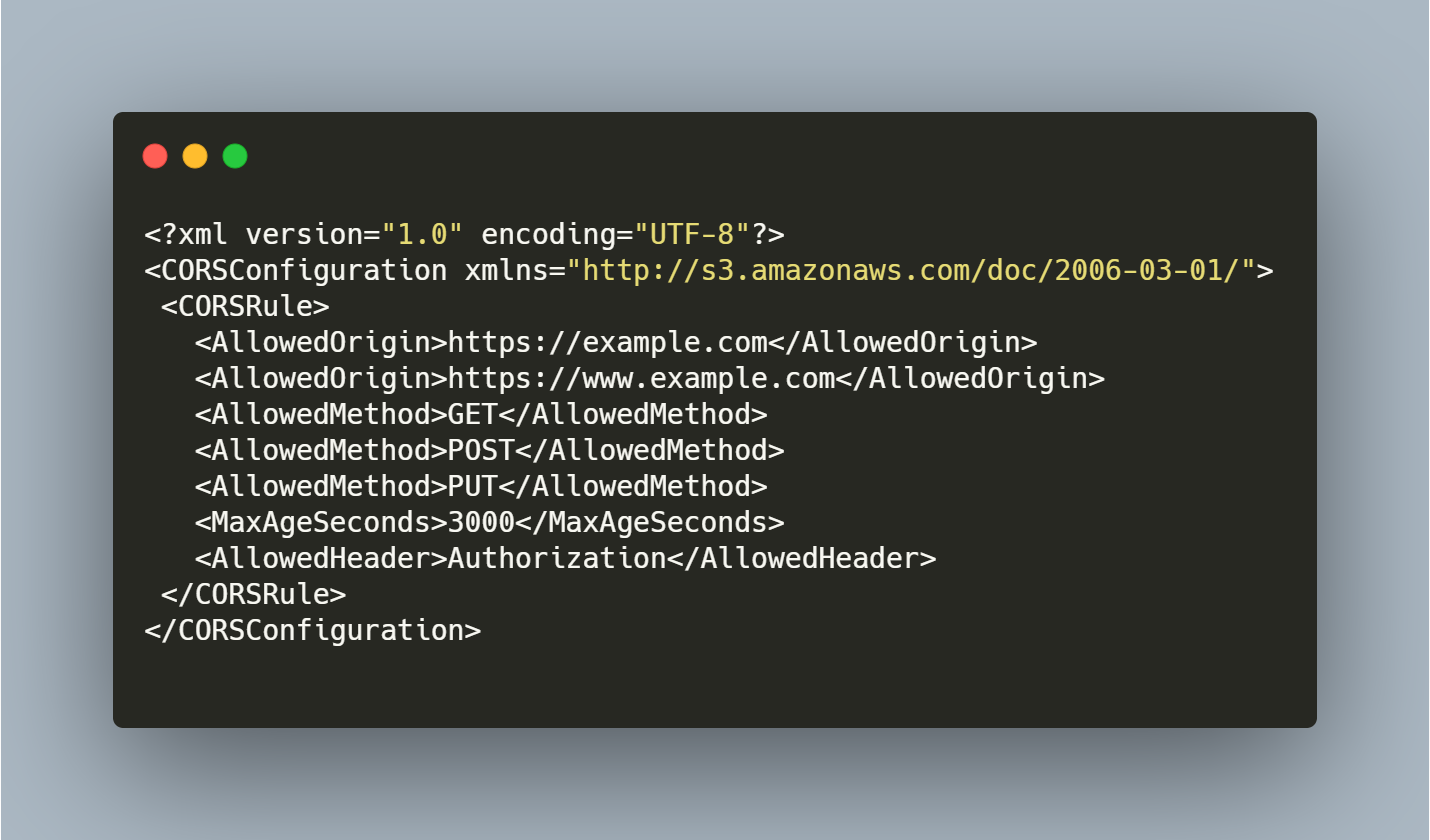
The website is only accessible via HTTPS request, but if you access via HTTP then you have to configure redirect policy and if the user comes to your website via www.example.com compared to example.com then it would be denied access to the bucket
To know more about the service please follow link

As a Director of Eternal Web Private Ltd an AWS consulting partner company, Nirav is responsible for its operations. AWS, cloud-computing and digital transformation are some of his favorite topics to talk about. His key focus is to help enterprises adopt technology, to solve their business problem with the right cloud solutions.
Have queries about your project idea or concept? Please drop in your project details to discuss with our AWS Global Cloud Infrastructure service specialists and consultants.