February 25, 2021 / Nirav Shah
The yum-cron is used to install security packages automatically in Linux systems so This provides an automatic upgrade to any yum based Linux operating system.
It allows a user to configure a cron job for the yum package manager.
So for that, you have to follow the OS-specific commands as given below:
So, how can we use it?
So It provides a proper way to check for updates, and download, and it applies security updates automatically.
The cron jobs for yum-cron package are active immediately after installing the package and there’s no extra configuration necessary. And The job will be run when daily at the time the cron jobs are set to run.
To install the yum-cron package.
# yum -y install yum-cron # chkconfig yum-cron on
Config automatic security updates
# vi /etc/yum/yum-cron.conf
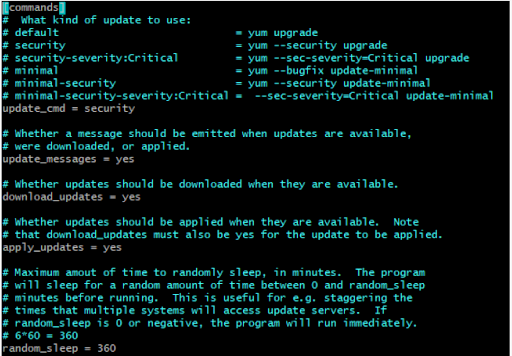
By default, this is set to default. Now edit and set the value to ‘security’.
update_cmd = security
We will be using the unattended update command below:
# yum --security upgrade
Next, change the value of update_messages from ‘no’ to ‘yes’.
update_cmd = security update_messages = yes download_updates = yes apply_updates = yes
Save and exit the config file.now start and enable the cron job,
#systemctl start yum-cron # systemctl enable yum-cron # systemctl status yum-cron
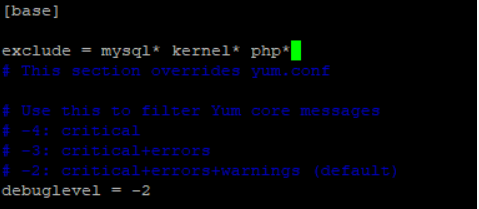
To exclude the packages follow below commands:
# vim /etc/yum/yum-cron.conf [base] exclude=kernel* mysql* php*
Restart the cron jobs and check the logs,
# systemctl restart yum-cron # systemctl status yum-cron # cat /var/log/yum.log | grep -i updated
Check the Automatic system updates that are controlled by a cron job service that runs daily and is stored in the /var/log/cron file.
# cat /var/log/cron | grep -i yum-daily
Now your redhat7 or CentOS 7 are fully configured for automatic security updates and there is no need for a manual method.

As a Director of Eternal Web Private Ltd an AWS consulting partner company, Nirav is responsible for its operations. AWS, cloud-computing and digital transformation are some of his favorite topics to talk about. His key focus is to help enterprises adopt technology, to solve their business problem with the right cloud solutions.
Have queries about your project idea or concept? Please drop in your project details to discuss with our AWS Global Cloud Infrastructure service specialists and consultants.