April 27, 2020 / Nirav Shah
In this blog we will show you how to secure s3 buckets in your AWS account. Let’s disccus the some practical techniques that you can use to deploy a S3 bucket.
Tip 1: You can secure your data using S3 encryption
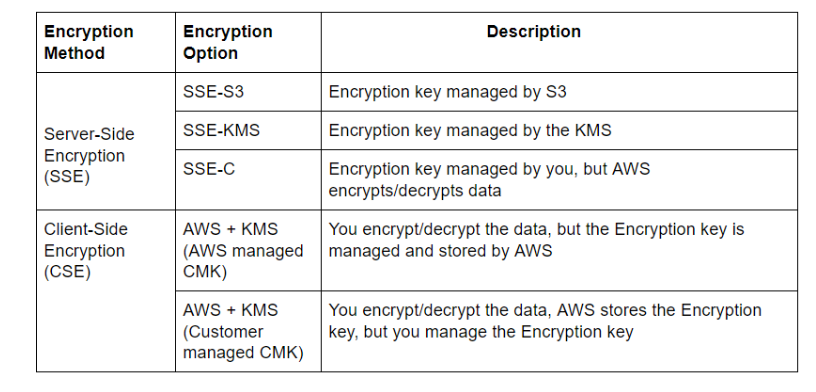
As we know that S3 offers two type of encryption options to protect your :
1) Server-Side Encryption:
In this type of encryption, AWS encrypts the raw data you send and stores it on its disks (on data centers). When you try to retrieve your data, AWS reads the data from its disks, decrypts, and sends it back to you.
2) Client-Side Encryption:
Using this type of encryption, you are the person who encrypts the data before sending it to AWS. Once you retrieve the data from AWS, you need to decrypt it.
As per your requirement you can choose one of the above options. Additionally, encryption could be categorized further based on key management requirements.
Tip 2: Restricting S3 access using bucket policies
Bucket policies allow you to be flexible and manage bucket access with fine-grained permissions. You can allow specific IP address or a IP range, so that only those users can access the buckets
Let us take an example:
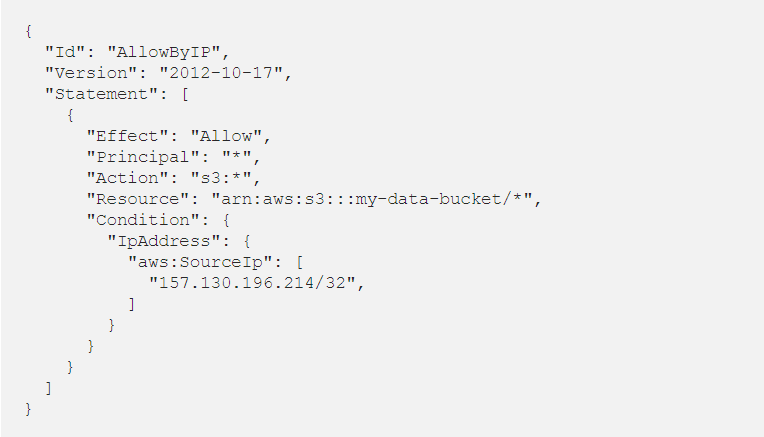
Here in the above example we have given a specific IP that is “157.130.196.214/24” so that only this IP is allowed to access the buckets.
Tip 3: Access Points to assign access policies
Amazon S3 Access Points you can create your own policy for each application , and so that Access point have different host name. Each access point gets its own AWS Identity and Access Management (IAM) policy. Access point policies are similar to bucket policies.
If you want to more about Access Points please visit below link
https://aws.amazon.com/s3/features/access-points/
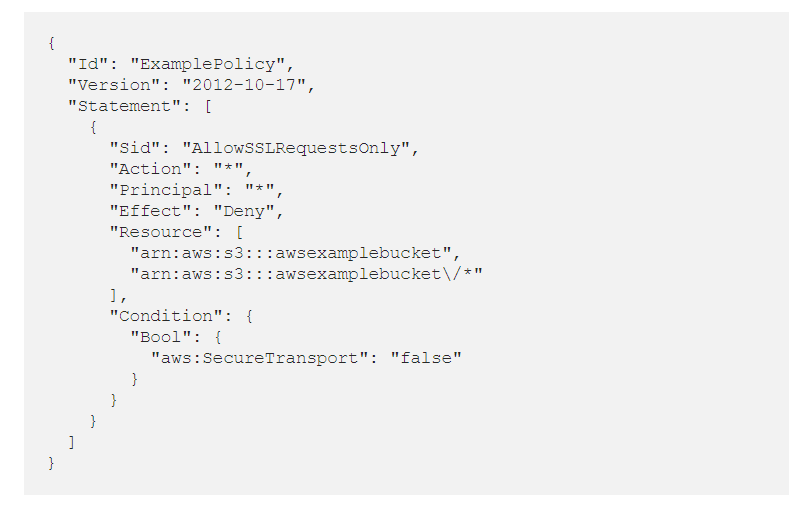
Tip 4: Mandate the use of SSL
S3 Bucket data can be accessed by using either HTTP or HTTPs. To protect the bucket from unsolicited access of bots we can use this feature.
Let us understand this with an example:
To create an end-to-end encryption on all traffic to a bucket, you can apply this bucket policy containing an explicit deny condition as shown here for an unsecured connection. All requests that do NOT use HTTPS will now be denied.
Tip 5 : Third-party AWS security tools
There is some third party that provides security tools to secure your data. They can save you time and keep the data secure at the same time. Some of the popular tools are:
1) Security Monkey
It is a tool developed by Netflix to monitor the AWS policy changes and alerts if it finds any insecure configurations.
If want to know more please visit this link: https://github.com/Netflix/security_monkey
2) Cloud Custodian
Cloud Custodianhelps you to manage resources in a cloud aligned with the best practices. In simple words, once you have identified the best practice, you can use this tool to scan the resources in the cloud to ensure that it is being met.
Conclusion
Monitoring S3 buckets is an essential and the most basic step towards ensuring better data security in your organization and AWS infrastructure. We hope that this blog would help you to secure the S3 buckets and data within.

As a Director of Eternal Web Private Ltd an AWS consulting partner company, Nirav is responsible for its operations. AWS, cloud-computing and digital transformation are some of his favorite topics to talk about. His key focus is to help enterprises adopt technology, to solve their business problem with the right cloud solutions.
Have queries about your project idea or concept? Please drop in your project details to discuss with our AWS Global Cloud Infrastructure service specialists and consultants.