November 18, 2020 / Nirav Shah
Wikipedia says, “Information security” sometimes shortened to InfoSec is the practice of preventing unauthorized access use disclosure, disruption, modification, inspection,
recording or destruction of information. Its primary focus is the balanced protection of the confidentiality, integrity, and availability of data, also known as the CIA triad while maintaining a focus on efficient policy implementation, all without hampering organization productivity.
With the CIA triad, making sure that only the right people can see certain data is confidentiality.
Being able to trust that the data hasn’t been changed inappropriately, is integrity. And being able to get out the data and use the system when you do need to is availability.
How do we take control of the data flow?
That brings us to the AAA model of security.
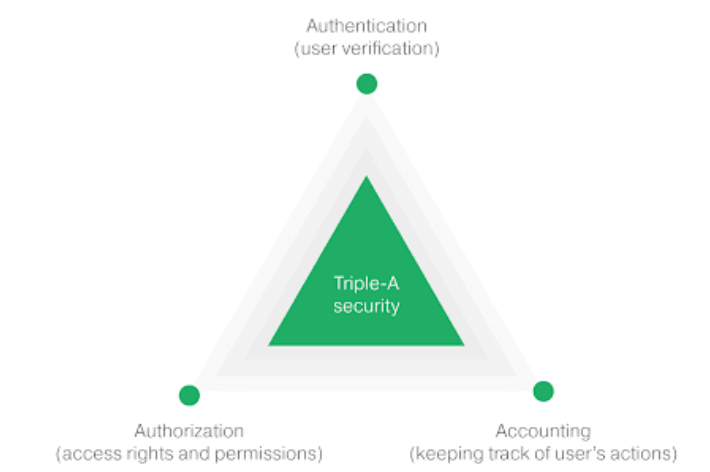
A – Authentication
This includes things like passwords, multi-factor authentication and single sign-on from another trusted system.
A – Authorization
Authorization asks are you allowed to do? And this includes both reading and writing.
A – Accounting
Is like “What did you do or what happened? This includes actions like writing or deleting data,
and it can also include viewing information.
How does data flow through a triple-A model?
Let’s understand for taking the example,
If the person tries to connect directly it is not possible, You need to be authenticated before you can access it.
So the first thing the user does is to connect to the authentication system. This system will validate the identity, and then sign a token for them.
Then also talk to the accounting system to record that this user did successfully log on. The user will then connect to the application and pass along the credentials from the authentication system. The application will check that the credentials are indeed signed by the authentication system.
Conclusion
In this post, we learnt about information security and AAA model of data flow.

As a Director of Eternal Web Private Ltd an AWS consulting partner company, Nirav is responsible for its operations. AWS, cloud-computing and digital transformation are some of his favorite topics to talk about. His key focus is to help enterprises adopt technology, to solve their business problem with the right cloud solutions.
Have queries about your project idea or concept? Please drop in your project details to discuss with our AWS Global Cloud Infrastructure service specialists and consultants.